What makes a good password?
When academics download examination paper templates in Guru, they choose a password to protect their documents on their local devices - but what makes a good password?
We recently introduced a new password meter to highlight good practice for academics choosing a password. It looks like the following for a bad password choice:
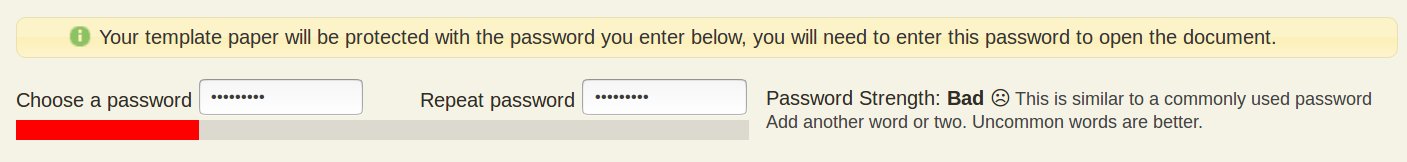
By adding a password meter, the hope is that users will strive to improve their passwords and see the following:
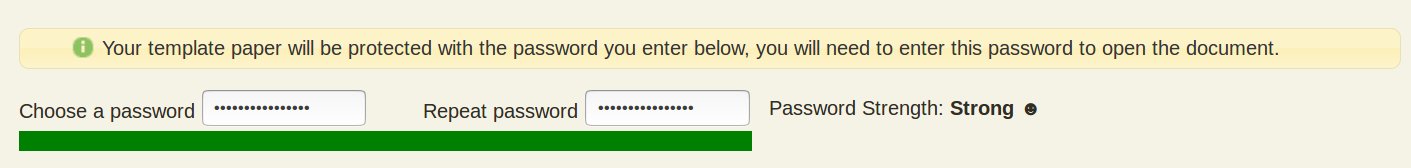
In our post on (“Reasons Why - Exam Security”) we talked about the significant benefits associated with enforcing the application of passwords on Word documents stored on user devices. Before examinations take place, most institutions (who aren’t using Guru) have hundreds or even thousands of devices containing un-encrypted examination papers. This increases the chance of examination paper compromise in the event of device loss or third-party hacking.
As Guru enforces password protection, this secures the documents in these scenarios. However, this does depend on the user choosing an appropriate password. There are some tools that will help recover a password from an encrypted Word document and these could be used by a third party to inappropriately access a document (if the device was also compromised). These tools will only compromise documents if an insecure password is chosen.
What makes a bad password?
Let’s take a look at some bad passwords as examples. Here are the top-ten, most-common passwords:
- password
- 123456
- 12345678
- abc123
- querty
- monkey
- letmein
- dragon
- 111111
- baseball
Perhaps you are breathing a sigh of relief - but don’t relax too soon! The following site keeps a list of (at the time of writing) 517,238,891 real world passwords that have been compromised. If your password is on this site, then it is either a bad password or has been compromised and you should use a different one!
WARNING: Even though this is a well respected site, you should use your own judgement on whether it is appropriate to actually put your password into any tools listed below. Perhaps try a similar password or just play around with different passwords!
Visit the site here: haveibeenpwned.com
How are passwords hacked?
There are two main ways that passwords are hacked:
-
Password Lists - Hackers try passwords from a list of common or compromised passwords. They might start with the top 100 passwords, then the top 10,000 and finally giant lists like the one shown above. If you are on these lists, then your password is easy to hack!
-
Brute Force - Hackers use tools to try combinations of characters. These start with ‘a’,’b’ etc. through to ‘Z’, then move on to ‘aa’, ‘ab’ etc. through to ‘ZZ’ and so on. To put this in perspective, a seven letter password with at least one uppercase character will take about 6 minutes to hack. A 12 character password (with uppercase characters) will take about 2 million years (good luck with that!). This site contains a useful tool: How Long to Hack my Password
So how do we choose a better password? Many websites (and companies) enforce specific password policies, such as the following:
- Provide at least one uppercase letter, one number and one special character
These policies have very marginal benefits at best and they introduce new problems. Humans when faced with policies like these tend to rely on patterns that are easy to remember. So now our user who wanted to use ‘letmein’ now uses something like the following:
- Letmein1!
- Letmein1*
- etc.
Each of these combinations are in turn compromised, despite meeting the requirements of these complex policies.
What makes a good password?
Our password meter uses a very impressive library by Dropbox known as ‘zxcvbn’ zxcvbn - Realistic Password Strength Estimation. This library uses a combination of analysing common words from most-used password lists and performing some brute force estimations. Bad passwords are those that are short or which use common words.
When we consider good passwords, they should be:
- Unique to one person
- Unique for each site (if one is compromised, then other site passwords are unaffected)
- Easy to remember
As humans, we are much better choosing passwords that are linguistic based. Here are some sample passwords (off the top of my head) together with estimated hacking times:
- groundappletree (19 thousand years)
- FourLittleSpiders (1.6 Trillion Years)
- TheSmallPurpleTree (87 Trillion Years)
These meet two of the requirements we stated. To provide uniqueness, we can take one of these passwords and customise it per site, by adding a uniqueness per site:
- FourLittleSpidersG (Google Login)
- FourLittleSpidersT (Twitter Login)
- FourLittleSpidersF (Facebook Login)
Of course, you might still need to put up with silly localised policies (e.g. special characters and numbers) which allow instantly cracked passwords like ‘Letmein1!’ but block these passwords that take trillions of years to crack. So let’s adapt our final chosen passwords:
- 4LittleSpidersG! (Google Login - 420 trillion years)
- 4LittleSpidersT! (Twitter Login - 420 trillion years)
- 4LittleSpidersF! (Facebook Login - 420 trillion years)
This should be more than enough time between the writing of examination papers and the live examination session!
Password Managers
We would be remiss not to mention password managers! Password managers are software applications that automatically create strong passwords for you, so you don’t have to worry about creating a reliable password every time you open a new account on a website. It stores your passwords in a single location which you can secure with one master password! This way, you only need to remember one password for all of your online accounts.
There are a number of good password managers out there such as ‘LastPass’, ‘KeePass’ and ‘Roboform’. It might be worth considering one of these moving forward.
